Set Up an Okta Application¶
Ensure that you have Administrator access to your Okta Account and Privacera.
Follow these steps to create and configure an Okta application for Single Sign-On (SSO):
Step 1: Log in to Your Okta Admin Console¶
- Log in using your administrator credentials.
Step 2: Create a New Application¶
- In the Admin Console, navigate to Applications from the left-side menu.
- Click on Applications under the Applications tab.
- On the Applications page, click Create App Integration.
Step 3: Choose SAML 2.0¶
- In the Create a New Application Integration dialog, select SAML 2.0 as the sign-in method.
- Click Next to proceed.
Step 4: General Settings¶
- In the General Settings section, provide a descriptive name for your application in the App name field.
For example:Privacera Portal SAML-SSO - (Optional) Upload a logo for the application if needed.
- Click Next to proceed to the SAML Settings page.
Step 5: Configure SAML Settings¶
-
In the SAML Settings section, fill in the following fields:
Field Value Example Single sign-on URL Self-Managed: https://PORTAL_HOST/saml/SSO
PrivaceraCloud:https://privaceracloud.com/SingleSignOnService/receiveResponseAudience URI (SP Entity ID) privacera_portal -
Scroll down to the Attribute Statements section to map user attributes:
Name Name format Value Optional/Required UserIdUnspecified user.loginRequired EmailUnspecified user.emailRequired FirstNameUnspecified user.firstNameOptional LastNameUnspecified user.lastNameOptional -
Click Next to proceed.
Step 6: Assign Users to the Application¶
- Go to the Assignments tab of the newly created application.
- Click Assign and select Assign to People or Assign to Groups.
- Choose the users or groups you want to assign and click Done.
Important
It is assumed that the user is already mapped with the appropriate groups before being assigned to the application in Okta.
Step 7: Optional - Configure Group Attribute¶
- In the Sign On tab, scroll down to Group Attribute Statements.
-
Add a group attribute statement to map user groups:
Name Filter Type Filter Value Example Description GroupStarts with EngineeringMatches all groups starting with "Engineering". Contains TeamMatches all groups containing the word "Team". Equals AdminGroupMatches only the group named "AdminGroup". Matches Regex ^(Engineering|Marketing|Sales).*Matches groups starting with "Engineering", "Marketing", or "Sales". -
Click Save to apply the group-based mapping.
Step 8: Feedback¶
- On the Feedback page, select I'm an Okta customer adding an internal app.
- Click Finish to complete the initial setup.
Step 9: Obtain Identity Provider Metadata and Embed Link¶
- Go to the Sign On tab of the newly created application.
- Scroll down to the Settings section.
- Click on Metadata URL to download the metadata XML file.
This file will be used for configuring the SSO in Privacera Portal. - Go to the General tab.
- Scroll down to the Embed Link section.
- Copy the Embed Link URL for the
Identity Provider Urlin Privacera Portal.
You have now successfully set up an Okta application for SAML SSO in the Okta console. This application is ready to be integrated with the Privacera Portal.
Configure Okta in your Privacera Account.¶
The steps to configure Okta integration in the Privacera Self-Managed (Portal).
Step 1: SSH into Privacera Instance¶
SSH into the instance where Privacera is installed.
Step 2: Navigate to Privacera Manager Directory¶
| Bash | |
|---|---|
Step 3: Copy the saml Sample Configuration File¶
Copy the sample saml configuration file to the custom configuration directory.
| Bash | |
|---|---|
Step 4: Edit the Configuration File¶
Open the configuration file using a text editor and update the required fields.
| Bash | |
|---|---|
Uncomment and edit the following properties:
If you have configured Group Attribute, uncomment and edit the following properties:
| YAML | |
|---|---|
Step 5: Upload the renamed metadata XML file to Privacera¶
- Locate the metadata file downloaded in Step 9, (usually in your
Downloadsfolder or the folder where you saved it). - Rename the file to
privacera-portal-aad-saml.xml
Step 6: Upload or Copy the File to Privacera Manager’s custom properties folder¶
Option 1: Using SCP (for Remote Servers)¶
- Open a terminal and run the following command to upload the file to the Privacera Manager’s custom properties folder: Replace
Bash <server-ip>with your server’s IP address anduserwith your username.
Option 2: Copy-Paste Locally¶
-
If the file is on the same server, move the
privacera-portal-aad-saml.xmlfile to the home directory. -
Use the following command to copy it to the custom properties folder
Ensure theBash privacera-portal-aad-saml.xmlfile is in the correct directory before running thecpcommand.
Step 7: Update Privacera Manager¶
Step 8: Optional - Restart Privacera Portal in an Azure Kubernetes Environment¶
If you are configuring SSL in an Azure Kubernetes environment, restart the Privacera Portal to apply the changes.
| Bash | |
|---|---|
Step 9: Optional - Role Mapping For Okta¶
Role mapping allows you to translate roles or groups from your Okta Identity Provider (IdP) into specific roles within Privacera. This ensures that users have the correct permissions and access when they log into Privacera.
What is Role Name Attributes?¶
This attribute in your Identity Provider (IdP) contains the user's roles or group information. It is used to identify the roles or groups the user belongs to in the IdP.
What is Role Mapping?¶
This configuration maps Identity Provider roles/groups to Privacera Portal roles. Matching roles are assigned to users; otherwise, the default role configured in the PORTAL_SSO_DEFAULT_USER_ROLE property in Privacera Manager is applied, or ROLE_USER if unspecified.
Tip
Assign Okta Identity Provider (IdP) roles or groups to Privacera Portal roles.
In Privacera, follow these steps to access the SAML Role mapping settings:
- Go to the Settings menu.
- Navigate to SSO Role Mapping.
- Click on SAML tab.
Reference image of Role Mapping form Privacera: 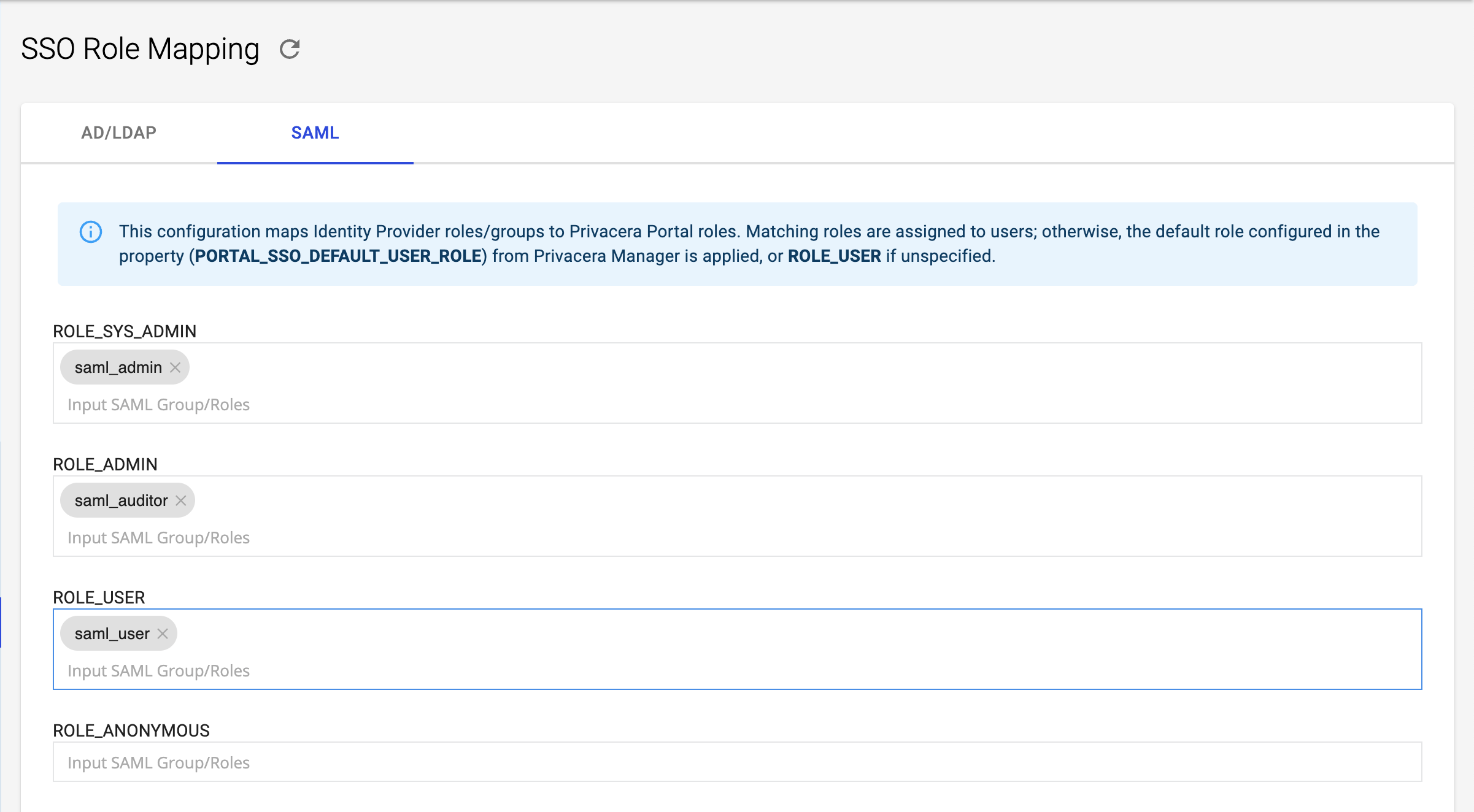
Example:¶
- Mapped Privacera Role:
ROLE_SYS_ADMIN - Identity Provider (IdP) Role or Group:
saml_admin
In this example, if a user has the saml_admin role in Okta, they will be automatically assigned the ROLE_SYS_ADMIN role in Privacera.
Step 10: Verify SSO Login¶
Once the setup is complete, navigate to the Privacera Portal login page. You should see an SSO Login button. Use it to log in with your Okta credentials.
In Privacera, follow these steps to access the Single Sign-On settings:
- Go to the Settings menu.
- Navigate to Identity.
- Click on Single Sign-On.
Reference image from PrivaceraCloud for better guidance: 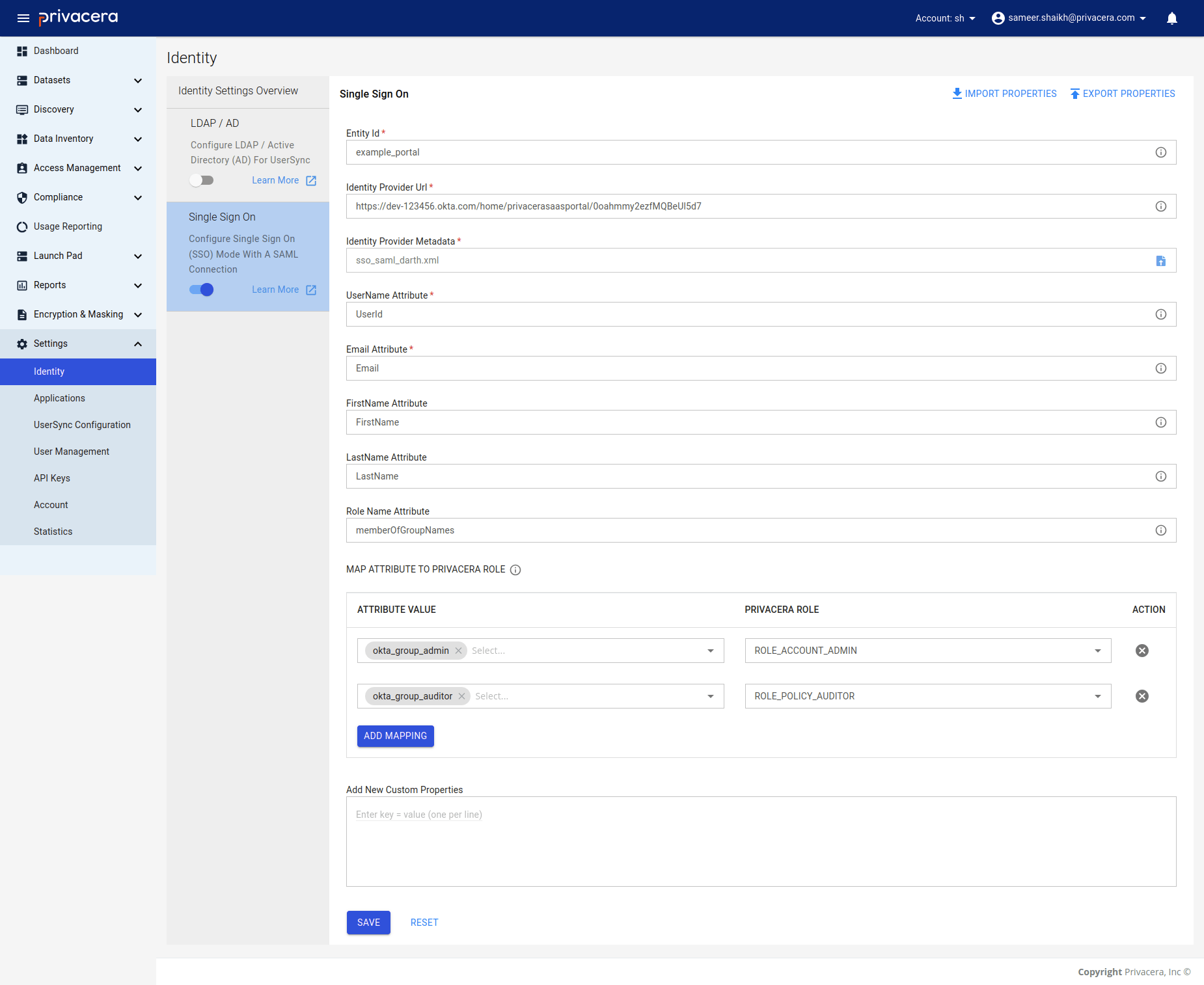
| Display Name | Description | Example Value | Optional/Required |
|---|---|---|---|
Entity Id | Entity ID for SAML configuration | privacera_portal | Required |
Identity Provider Url | Identity Provider URL | https://dev-123456.okta.com/home/privacerasaasportal/0oahmmy2ezfMQBeUl5d7 | Required |
Identity Provider Metadata | Metadata (XML file) | sso_saml_darth.xml | Required |
UserId | UserName attribute for SAML user | UserName | Required |
Email | Email attribute for SAML user | Email | Required |
FirstName | FirstName attribute for SAML user | FirstName | Optional |
LastName | LastName attribute for SAML user | LastName | Optional |
Important
- Entity ID: Used to configure the Identity Provider (IdP).
- Identity Provider URL: The URL obtained in Step 9, where users will be redirected for SSO login.
- Identity Provider Metadata: Use the Metadata XML file downloaded in Step 9 for seamless SSO configuration.
- User Attributes: Ensure that the correct user attributes (
UserId,Email,FirstName,LastName) are mapped from Okta to Privacera.
These variables ensure seamless integration between Okta and Privacera for SAML-SSO.
Role Mapping For Okta¶
Role mapping allows you to translate roles or groups from your Identity Provider (IdP) — such as Okta, Ping Identity, OneLogin, etc. — into specific roles within Privacera. This is crucial for ensuring that users have the correct permissions and access when they log into Privacera.
What is Role Name Attributes?¶
This attribute in your Identity Provider (IdP) contains the user’s roles or group information. It identifies the roles or groups the user belongs to in the Identity Provider (IdP).
What is Role Mapping?¶
This configuration maps roles or groups from the Identity Provider (IdP) to corresponding roles in Privacera.If a specific role from the IdP matches a role defined in the role mapping configuration, that role is assigned to the user in Privacera. If no mapping is defined, the default role, ROLE_USER, is automatically assigned to the user.
| Variable Name | Description | Example |
|---|---|---|
Role Name Attribute | Role name attributes for user. | department |
Role Mapping | Role mapping for user. | Identity Provider (IdP) Role: example_role → Example Role: ACCOUNT_ROLE |
Reference image of Role Mapping form PrivaceraCloud: 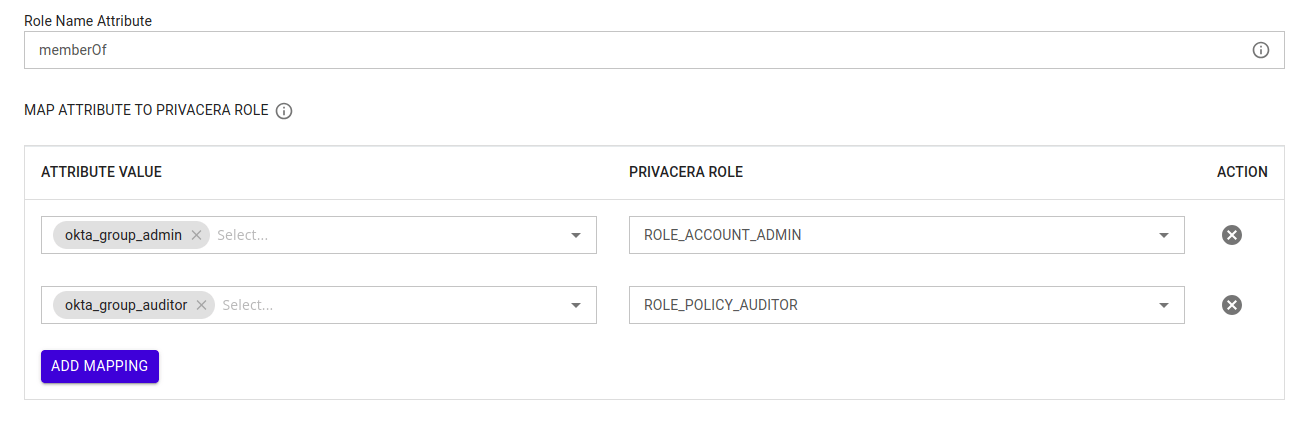
Example:¶
- Identity Provider (IdP) Role or Group:
okta_role_admin - Mapped Privacera Role:
ACCOUNT_ADMIN
In this example, if a user has the role okta_role_admin in Okta, they will automatically be assigned the ACCOUNT_ADMIN role in Privacera.
Important
New Users:
Role mapping applies only to newly created users after the mapping has been configured.
By properly configuring role mapping, you ensure that users are granted appropriate access levels within Privacera based on their roles or group memberships from the Identity Provider (IdP). This simplifies user management and ensures seamless integration with your organization’s existing identity infrastructure.
Once the configuration is complete, you can test the setup by attempting to log in to PrivaceraCloud using your Okta credentials. This will help verify that the Single Sign-On (SSO) integration is working correctly.