LDAP Configuration in Privacera¶
The steps to configure LDAP integration in the Privacera Self-Managed (Portal).
Step 1: SSH into Privacera Instance¶
SSH into the instance where Privacera is installed.
Step 2: Navigate to Privacera Manager Directory¶
| Bash | |
|---|---|
Step 3: Copy the LDAP Sample Configuration File¶
Copy the sample LDAP configuration file to the custom configuration directory.
| Bash | |
|---|---|
Step 4: Edit the Configuration File¶
Open the configuration file using a text editor and update the required fields.
| Bash | |
|---|---|
To configure an SSL-enabled LDAP server, Privacera requires an SSL certificate. You have these options for setting it up:
-
Set the Privacera property
PORTAL_LDAP_SSL_ENABLED: "true"to enable SSL for the LDAP server. -
Option 1: Allow Privacera Manager to automatically download and create the certificate based on the LDAP server URL. Set the Privacera property
PORTAL_LDAP_SSL_PM_GEN_TS: "true". -
Option 2: Manually configure a truststore on the Privacera server that contains the certificate of the LDAP server. Set the Privacera property
PORTAL_LDAP_SSL_PM_GEN_TS: "false".
Uncomment and edit the following properties:
Step 5: Update Privacera Manager¶
After making the changes, update Privacera Manager to apply the new configuration.
Step 6: Optional - Add Role Mapping¶
Role mapping allows you to translate roles or groups from your Identity Provider (IdP), such as LDAP, into specific roles within Privacera. This is crucial for ensuring that users have the correct permissions and access when they log into Privacera.
In Privacera, follow these steps to access the LDAP/AD Role mapping settings:
- Go to the Settings menu.
- Navigate to SSO Role Mapping.
- Click on LDAP/AD tab.
Reference image from Privacera for better guidance: 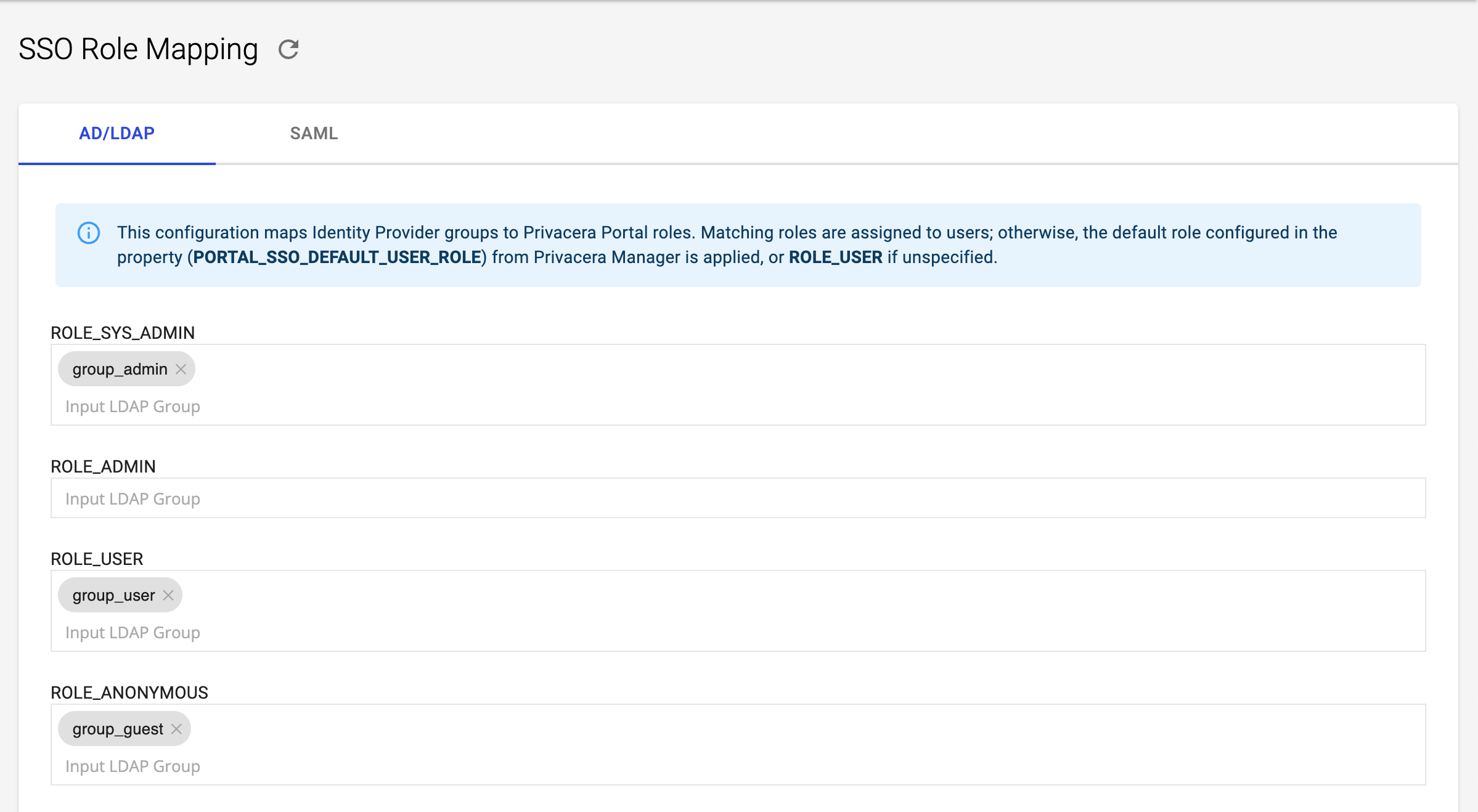
Example:¶
- Identity Provider (IdP) Role or Group:
group_admin - Mapped Privacera Role:
ROLE_SYS_ADMIN
In this example, if a user has the role group_admin in LDAP/AD, they will be automatically assigned the ROLE_SYS_ADMIN role in Privacera.
Important
This configuration maps Identity Provider roles/groups to Privacera Portal roles. Matching roles are assigned to users; otherwise, The default role configured in the PORTAL_SSO_DEFAULT_USER_ROLE property in Privacera Manager is applied, Or ROLE_USER if unspecified.
Step 7: Verify the Configuration¶
Once the update is complete, validate the configuration by accessing the Privacera Portal and ensuring that LDAP integration is working as expected.
In Privacera, follow these steps to access the LDAP/AD settings:
- Go to the Settings menu.
- Navigate to Identity.
- Click on LDAP/AD.
Reference image from privaceraCloud for better guidance: 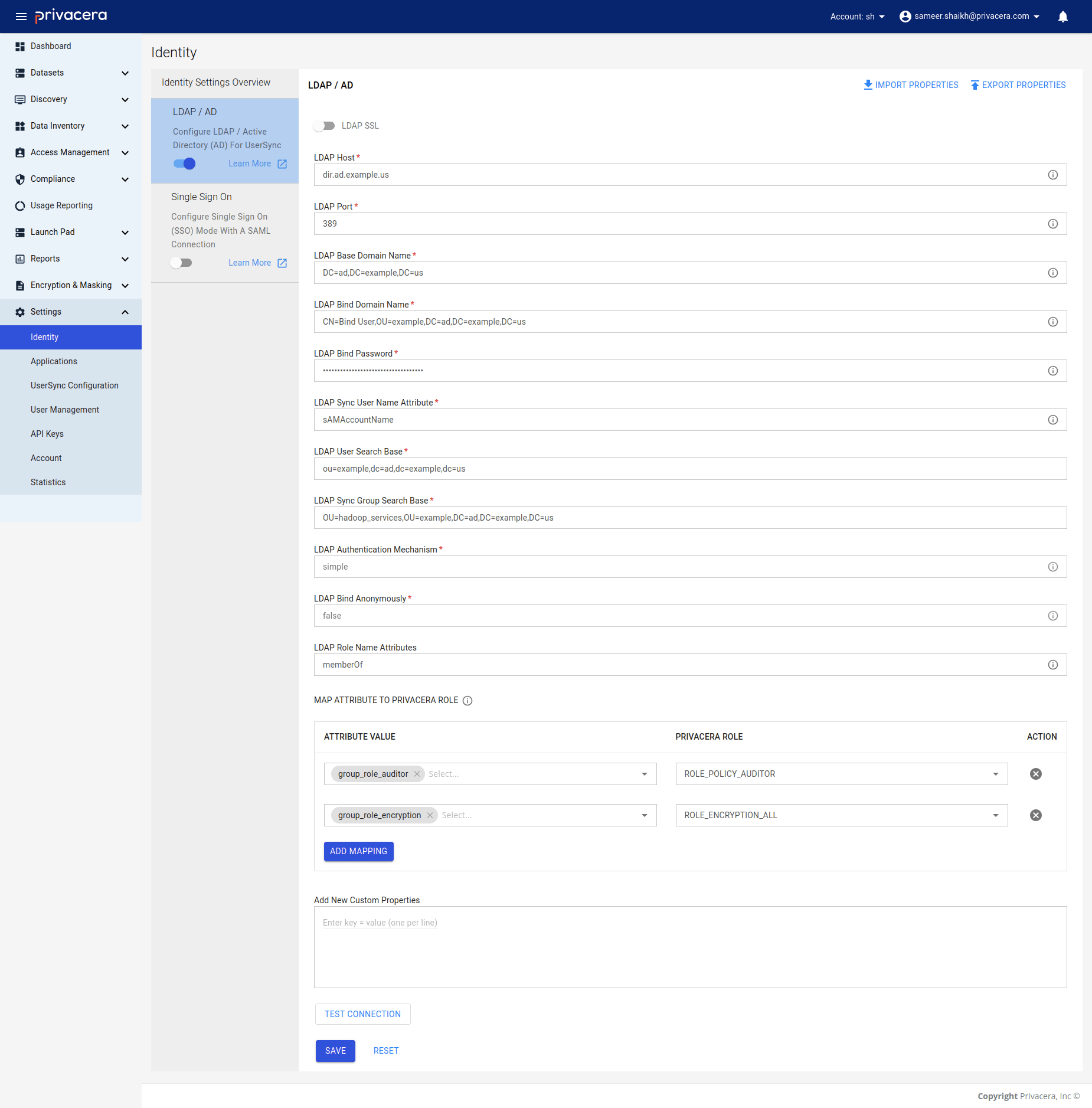
| Variable Name | Description | Example |
|---|---|---|
LDAP_URL | DNS of LDAP Host. | xxx.example.com:983 |
LDAP_PORT | Default ports: 389 for LDAP; 636 for LDAPS | 389 |
PORTAL_LDAP_BASE_DN | Search starting point in LDAP tree for user authentication. | dc=ad,dc=example,dc=us |
LDAP_BIND_DN | Domain administrator or service identity for LDAP/LDAP server. | CN=Bind User,OU=example,DC=ad,DC=example,DC=us |
LDAP_BIND_PASSWORD | Password for LDAP Bind Domain Name (Domain administrator). | password |
LDAP_USERNAME_ATTRIBUTE | LDAP attribute for the login name. | sAMAccountName |
LDAP_USER_SEARCH_BASE | The base distinguished name for user searches in LDAP. | ou=example,dc=ad,dc=example,dc=us |
LDAP_GROUP_SEARCH_BASE | The base distinguished name for group searches in LDAP. | OU=hadoop_services,OU=example,DC=ad,DC=example,DC=us |
LDAP_AUTHENTICATION_MECHANISM | Authentication method ‘simple’ is supported. | simple |
LDAP_BIND_ANONYMOUSLY | Anonymous binding is not supported. | false |
Role Mapping for LDAP¶
Role mapping allows you to translate roles or groups from your Identity Provider (IdP), such as LDAP, into specific roles within Privacera. This is crucial for ensuring that users have the correct permissions and access when they log into Privacera.
What is Role Name Attributes?¶
This attribute in your Identity Provider (IdP) contains the user’s roles or group information. It is used to identify the roles or groups the user belongs to in the IdP.
What is Role Mapping?¶
This configuration maps roles or groups from the Identity Provider (IdP) to the corresponding roles in Privacera. If a specific role from the Identity Provider (IdP) matches a role defined in the role mapping configuration, that role is assigned to the user in Privacera. If no mapping is defined, the default role, ROLE_USER, is automatically assigned.
| Variable Name | Description | Example |
|---|---|---|
LDAP_ROLE_NAME_ATTRIBUTES | Role name attributes for LDAP user. | memberOf |
LDAP_ROLE_MAPPING | Role mapping for LDAP user. | Identity Provider (IdP) Role: ldap_role → Example Role: ACCOUNT_ROLE |
Reference image of Role Mapping from privaceraCloud: 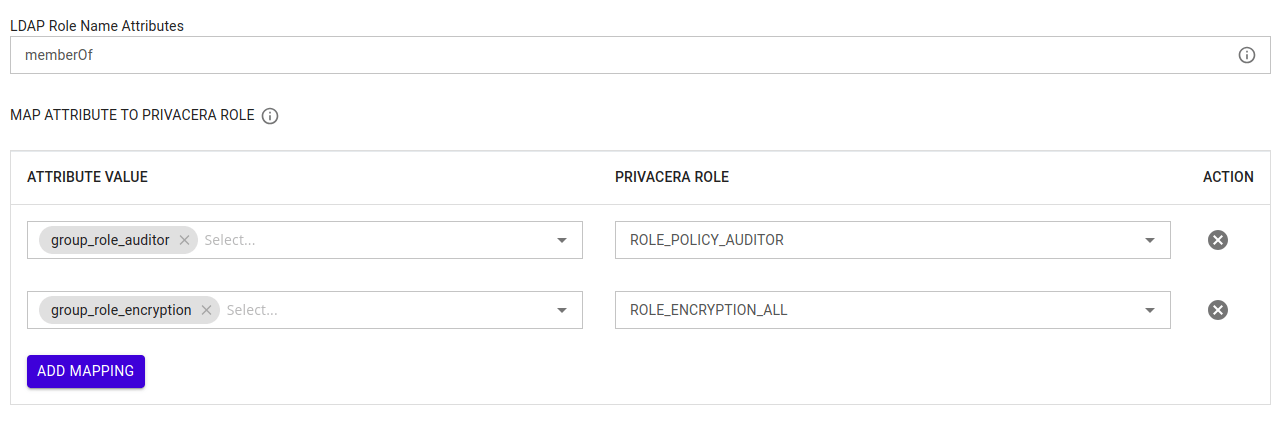
Example:¶
- Identity Provider (IdP) Role or Group:
group_role_admin - Mapped Privacera Role:
ACCOUNT_ADMIN
In this example, if a user has the group_role_admin role in LDAP, they will be automatically assigned the ACCOUNT_ADMIN role in Privacera.
Important
New Users:
Role mapping only applies to newly created users after the mapping has been configured.
By properly configuring role mapping, you ensure that users are granted the appropriate access levels within Privacera based on their roles or group memberships in the Identity Provider (IdP). This simplifies user management and ensures seamless integration with your organization’s existing identity infrastructure.
Once the configuration is complete, you can test the setup by attempting to log in to PrivaceraCloud with your LDAP credentials. This will help verify that the Single Sign-On (SSO) integration is working correctly.
- Prev