Connect to PrivaceraCloud over AWS PrivateLink¶
Overview¶
PrivaceraCloud supports AWS PrivateLink. This enables secure, private access to Privacera services from your AWS Virtual Private Cloud (VPC) — without exposing traffic to the public internet.
Using AWS PrivateLink, you create interface VPC endpoints in your AWS account that connect directly to Privacera's VPC Endpoint Services. This allows communication with Privacera services such as the Portal and API Server. Each service has a unique PrivateLink service name and a corresponding Private DNS hostname, accessible only from whitelisted AWS accounts.
Pre-requisites¶
Before you begin, make sure the following steps are completed:
1. Share Your AWS Account Details for Whitelisting¶
To connect to Privacera’s services over AWS PrivateLink, you need to request access. Raise a Support Ticket with the following information:
| Field | Description |
|---|---|
| AWS Account ID | The 12-digit AWS account ID where the VPC endpoints will be created. |
| AWS Region(s) | Specify the AWS region(s) where you plan to deploy the VPC endpoint(s), e.g., us-east-1, us-west-2. |
| Required Services | List the Privacera services for which you need PrivateLink access (e.g., Portal, API Server). |
| Contact Email (optional) | Provide a technical point of contact (email) for coordination. |
| VPC Endpoint Usage Timeline (optional) | Let us know when you expect to create the endpoint, in case priority is needed. |
Supported AWS Regions:
- us-east-1
- us-west-2
You must create endpoints in the same region as your workloads that need to access Privacera services.
Setup Instructions¶
Step 1: Log in to AWS Console¶
a. Go to: https://console.aws.amazon.com/ b. Switch to the desired region (us-east-1 or us-west-2).
Step 2: Create a VPC Endpoint¶
a. In the AWS Console, navigate to VPC Console → Endpoints → Create Endpoint.
b. Under Service category, select Other endpoint services.

c. Copy the correct PrivateLink service name from the table below and paste it in the Service Name field.
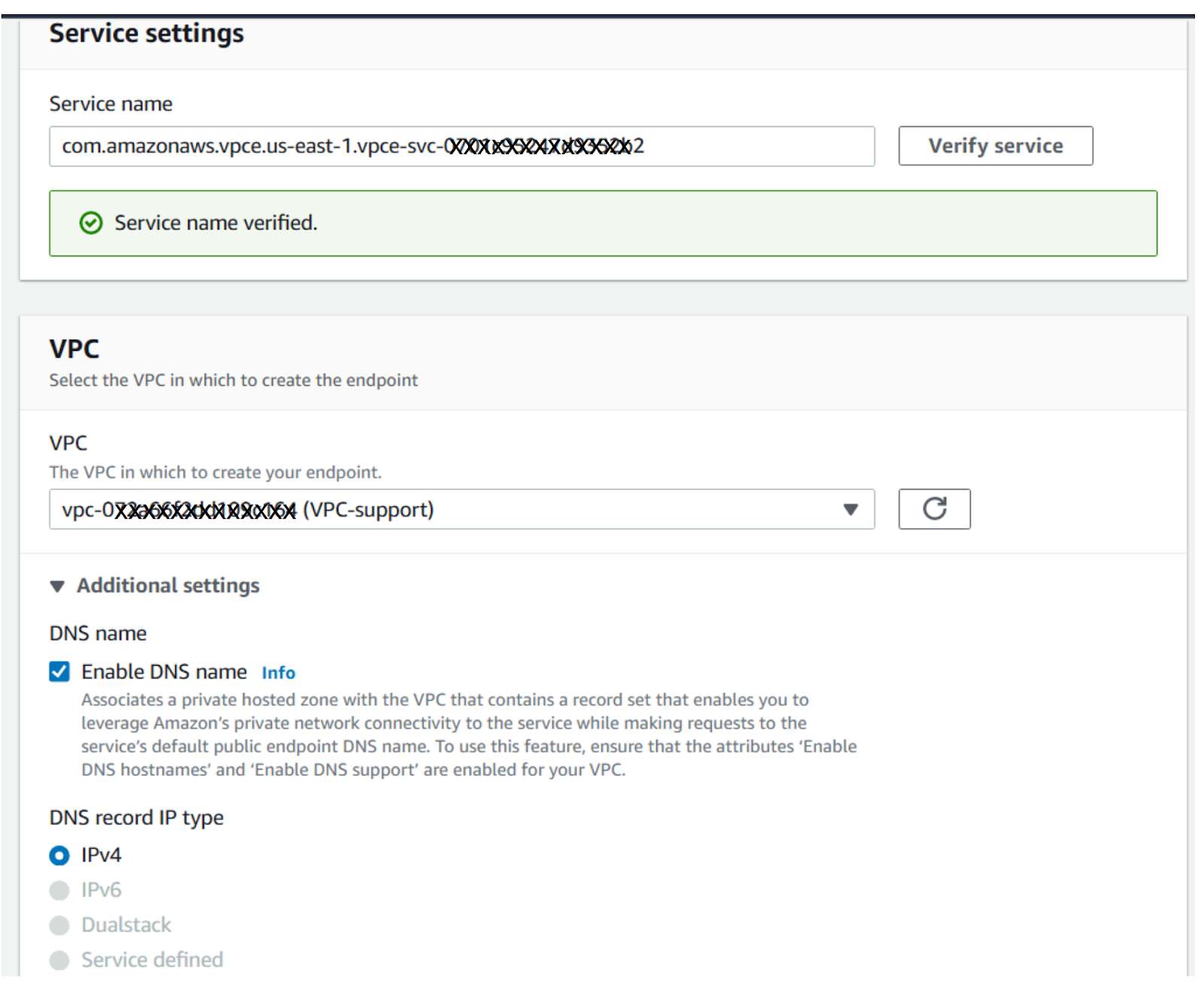
Step 3: Verify the Service Name¶
a. Enter the Service Name, then click Verify.
b. If verification fails, contact Privacera Support.
Step 4: Configure Endpoint Details¶
a. Choose the target VPC and one or more subnets where access to Privacera is needed.
b. Assign a security group that allows inbound TCP traffic on port 443 (HTTPS).
Step 5: Create the Endpoint¶
a. Click Create Endpoint. b. Once created, the status will be PendingAcceptance.
Step 6: Notify Privacera Support¶
a. Inform support that your endpoint is ready for approval.
b. Privacera will accept the connection request. After that, the endpoint status will change to Available.
Step 7: Enable Private DNS¶
a. Open your VPC Endpoint details.
b. Ensure the Enable DNS name checkbox is checked.
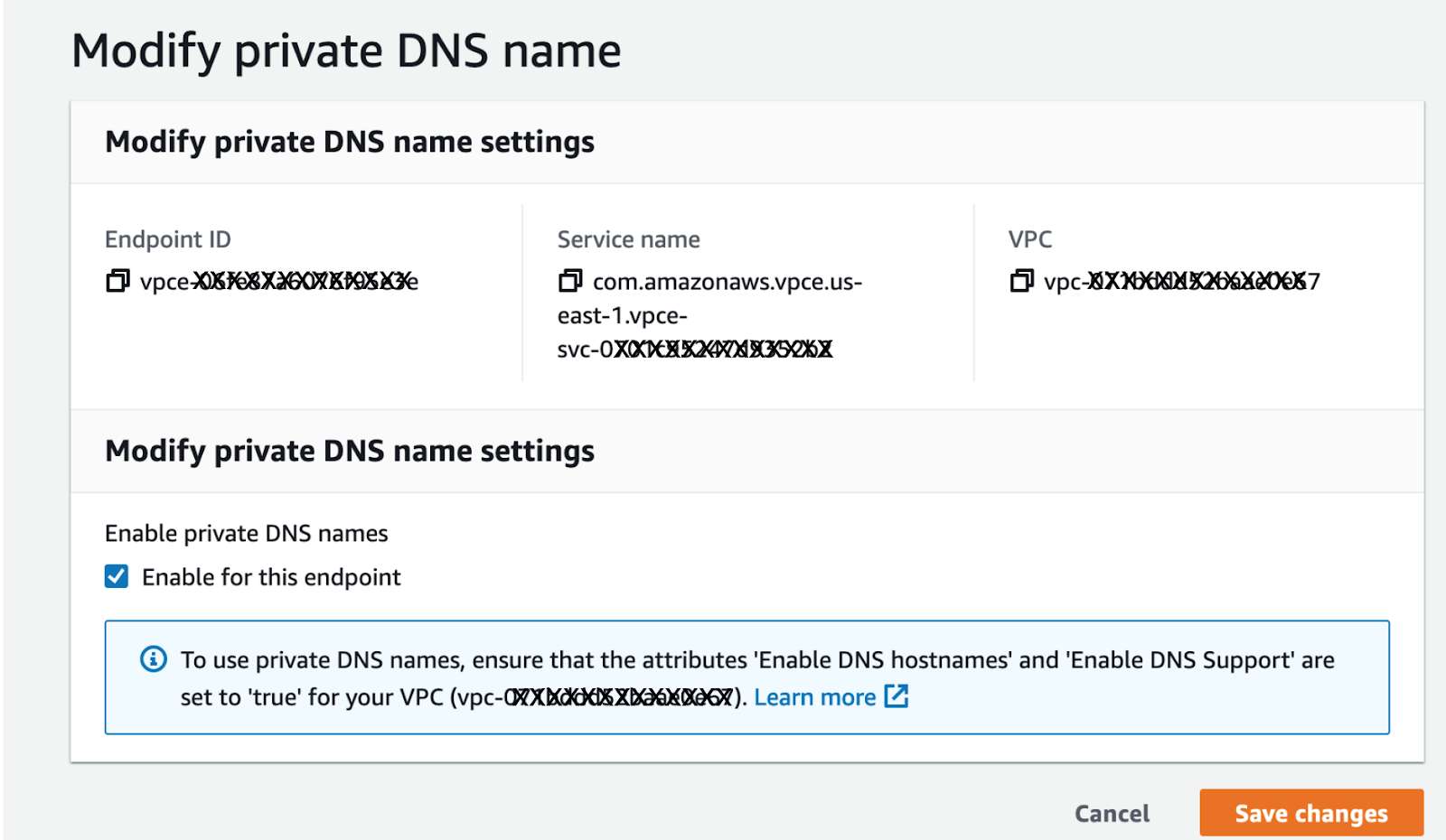
c. This enables internal name resolution using the Private DNS provided by Privacera.
Step 8: Configure Your Application¶
Update your Privacera applications running inside your VPC to use AWS PrivateLink:
a. Replace the public service URLs with the corresponding Private DNS names listed above.
b. Ensure that DNS resolution inside your VPC is correctly routing to the VPC endpoint using Private DNS.
This configuration ensures all application traffic to Privacera services is routed securely and privately over AWS PrivateLink, avoiding exposure to the public internet.
Available PrivateLink Services¶
| Region | Service | PrivateLink Service Name | Private DNS Name |
|---|---|---|---|
| us-east-1 | Portal | com.amazonaws.vpce.us-east-1.vpce-svc-080503731843a07e4 | vpce-us-east-1-aws-portal.privaceracloud.com |
| us-east-1 | API Server | com.amazonaws.vpce.us-east-1.vpce-svc-0985ba458a56c8e1a | vpce-us-east-1-aws-api.privaceracloud.com |
| us-west-2 | Portal | com.amazonaws.vpce.us-west-2.vpce-svc-07ddd3eda676ee551 | vpce-us-west-2-aws-portal.privaceracloud.com |
| us-west-2 | API Server | com.amazonaws.vpce.us-west-2.vpce-svc-01c3c3fb05cbb8ef4 | vpce-us-west-2-aws-api.privaceracloud.com |
Tips & Best Practices¶
a. If using custom DNS or on-prem resolvers, ensure DNS forwarding is configured correctly to resolve Private DNS names via Route 53.
b. Use AWS CloudWatch Logs or VPC Flow Logs to monitor traffic and troubleshoot connection issues.
Support¶
If you need help or want to request access to more endpoint services:
a. Contact Privacera Support at: support@privacera.com
b. Include the following in your message: - Your AWS account ID - The region you’re working in - The name of the endpoint service you’re trying to access.
- Prev topic: User Guide