Native Tag Masking¶
This document provides information on how to use the native tag masking feature in BigQuery Connector.
BigQuery's native masking feature empowers users to implement data masking at the column level seamlessly. This functionality enables selective obscuring of column data for specific user groups while maintaining their access to the column itself.
BigQuery Native Masking Workflow. 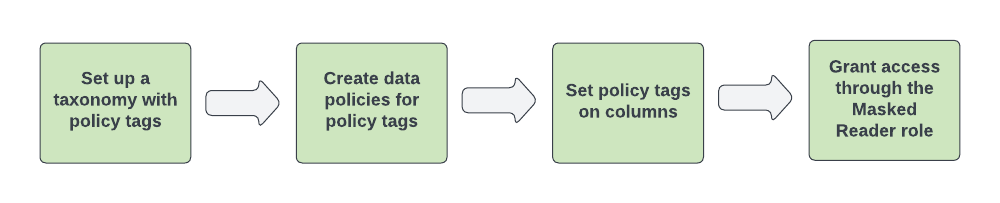
Available Guides¶
Prerequisites¶
- Taxonomy creation : To create a tag in the Privacera portal, a taxonomyId must be provided as part of the tag attributes. Therefore, creating a taxonomy is a prerequisite for configuring the connector. The taxonomy in BigQuery needs to be manually created by the end-user, as the connector depends on it for generating policy tags. Create Taxonomy in BigQuery
- Custom Masking: To create a masking policy using a custom routine (UDF), the routine must already exist in the project where the masking policy is to be applied. Additionally, users are required to provide the routine path.
The Path of routine must follow following format:
| Text Only | |
|---|---|
Key Considerations:
- The routine must be present within the same project where the masking policy is being created.
- The path format should be strictly followed to ensure proper integration of the routine with the masking policy.
- Ensure that
<project-id>is accurate. - Ensure that
<dataset-name>is valid in the project. - Ensure that
<routine-Name>matches exactly with the routine created in the dataset.
- Ensure that
- If the provided routine path is not supported or the routine is not found, the connector will throw an error and create the masking policy in BigQuery with the default masking.
Use Cases¶
Applying Tag-Based Masking Policy for End User¶
This guide outlines the steps to create a tag-based masking policy in Privacera for end users, including creating tag definitions, mapping resources, and applying access and masking policies.
Step 1: Create Tag Definition in Privacera¶
-
Login to Privacera Portal:
- Navigate to the Access Management section and select Tag Management.
-
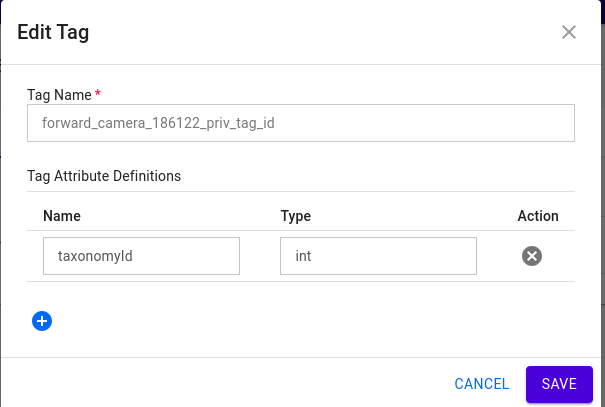
Create Tag:
- Click on Create Tag.
-
Enter the Tag Name and Tag Attribute Definition as described below:
-
Tag Name Format:The format for the tag name should be as follows:
Where:Text Only - project-id is the identifier for your project.
- priv_tag is a fixed separator between the project name and tag name.
- tagName is the name of the specific tag you are creating.
- If the project name contains a hyphen ("-"), replace it with an underscore ("_") when creating the tag definition in Privacera. This ensures consistency in the naming convention.
-
Add attribute definition to accept taxonomyId while creating tag.
- Click on Add Attribute Definition.
- Enter the Attribute Name as
taxonomyId. - Enter the Attribute Type as
int. - Click on Save.
Step 2: Create Tag Resource Mapping in Privacera¶
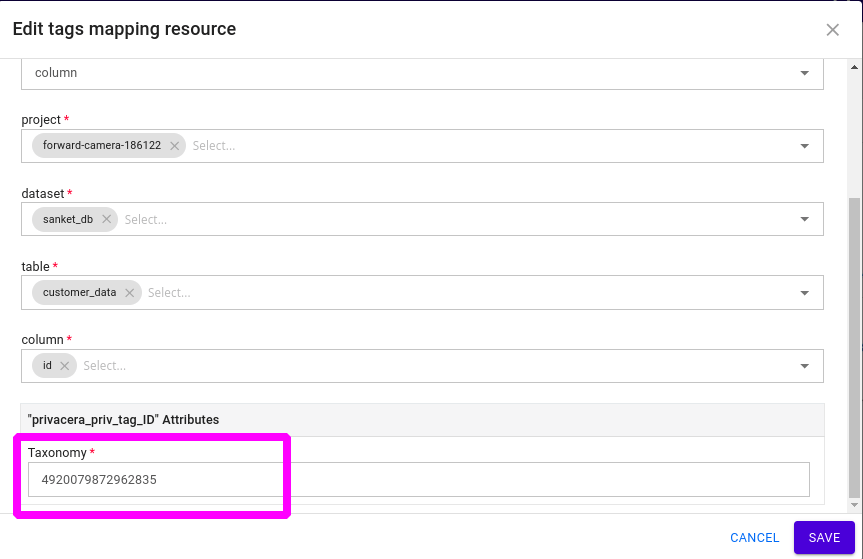
- Navigate to Tag Management:
- Go to the Tag Management section in the Privacera portal and click on the Tag Resource button.
- Specify Tag and Resource:
- Select the tag you created earlier and specify the resource to map the tag.
- Tag Resource Mapping does not work when resource name has wildcard (*)
-
Add Taxonomy ID:
- In the Taxonomy Attribute, enter the taxonomyID. The value of taxonomyID should be the Policy Tag Taxonomy ID created in Google Cloud BigQuery.
- Click on Save.
Step 3: Create Resource-Based Policies in Privacera¶
- Create Resource-Based Policy for Job Creation Access:
- Policy Type: Resource-Based Policy
- Resource: Project
- Permission: Job Create
- Create Resource-Based Policy for Query Permission on Table:
- Policy Type: Resource-Based Policy:
- Resource: Table
- Permission: Query
Step 4: Create Tag-Based Masking Policy in Privacera¶
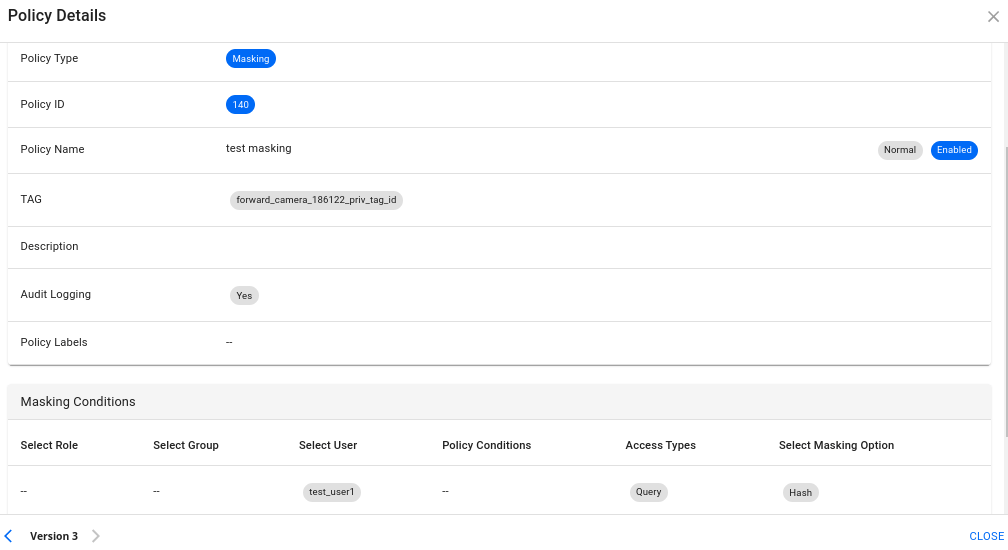
- Create Tag Masking Policy:
- Tag: forward_camera_186122_priv_tag_id
- Users: test_user1
- Access Types: bigquery
- Masking Option: Nullify
This policy will mask the data for test_user1 by nullifying the values. This ensures sensitive data is masked for the specified user.
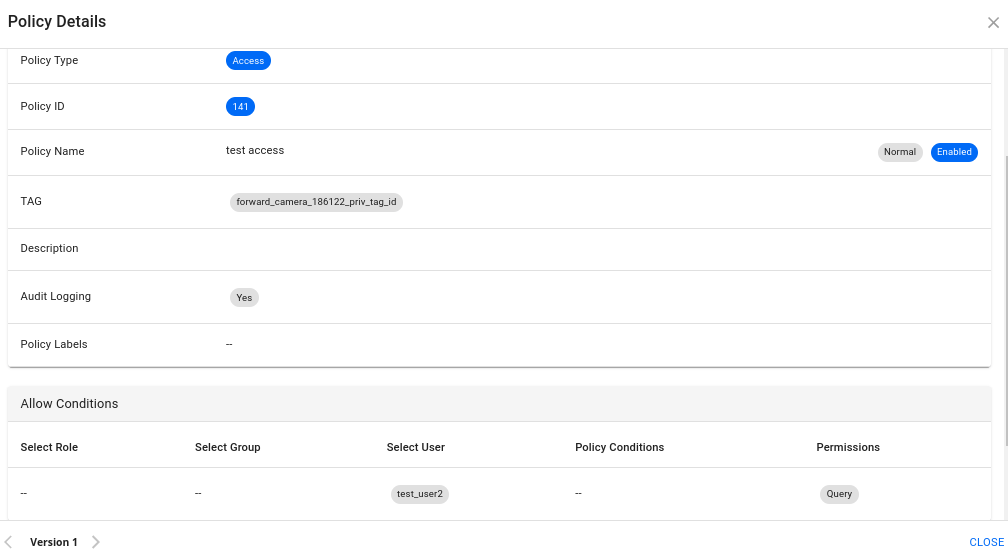
Step 5: Create Tag-Based Access Policy in Privacera¶
-
Create Tag Access Policy:
- Tag:
forward_camera_186122_priv_tag_id - Users:
test_user2 - Permission:
Query
- Tag:
This policy will grant test_user2 access to query the data tagged with forward_camera_186122_priv_tag_id. Since test_user2 has the appropriate access policy, they will be able to see the unmasked data, regardless of any masking policies applied for other users.
Note: The access granted to test_user2 will bypass any masking policies for that specific tag, allowing full visibility of the data.
Limitations¶
-
BigQuery Column-Level Security Behavior: In BigQuery, if an end user needs access to a column that has a tag attached, they must either be included in the tag-based masking policy or have permissions through a tag-based access policy. This is a key requirement for managing column-level security with tags in BigQuery.
Reference: BigQuery Column-Level Security -
Prerequisite - Taxonomy Creation:
- To create a tag in the Privacera portal, a taxonomyId must be provided as part of the tag attributes. Therefore, creating a taxonomy is a prerequisite for configuring the connector.
- The taxonomy in BigQuery must be manually created by the end-user, as the connector depends on it for generating policy tags. Reference: Create Taxonomy in BigQuery
-
Location Supported in Connector’s Configuration:
- BigQuery resources and taxonomies can be created across various locations. However, the PolicySync connector currently supports access control management for resources within a single location.
- The connector does not support the management of resources across multiple locations concurrently.
-
Tag-Based Masking on Service Account is Not Supported:
- The connector does not support tag-based masking policies for service accounts. Service accounts cannot be used to apply or manage tag-based masking policies in the connector.
-
Taxonomy Must Be Created in the Same Project:
- The taxonomy used for creating tags must be created within the same project where the resources (such as datasets or tables) are located. The connector relies on this for the proper mapping of tags to resources.