Native Tag Masking in BigQuery¶
This document provides information on how to use the native tag masking feature in BigQuery Connector.
BigQuery's native masking feature empowers users to implement data masking at the column level seamlessly. This functionality enables selective obscuring of column data for specific user groups while maintaining their access to the column itself.
Overview: Native Tag-Based Masking with Privacera¶
Introduction¶
This section provides an end-to-end overview of how BigQuery native tag-based masking/access works using Privacera integrated with Google Cloud Platform (GCP). It explains what actions are performed manually on GCP vs. what Privacera automates, helping users understand the complete flow.
Sequence Diagram¶
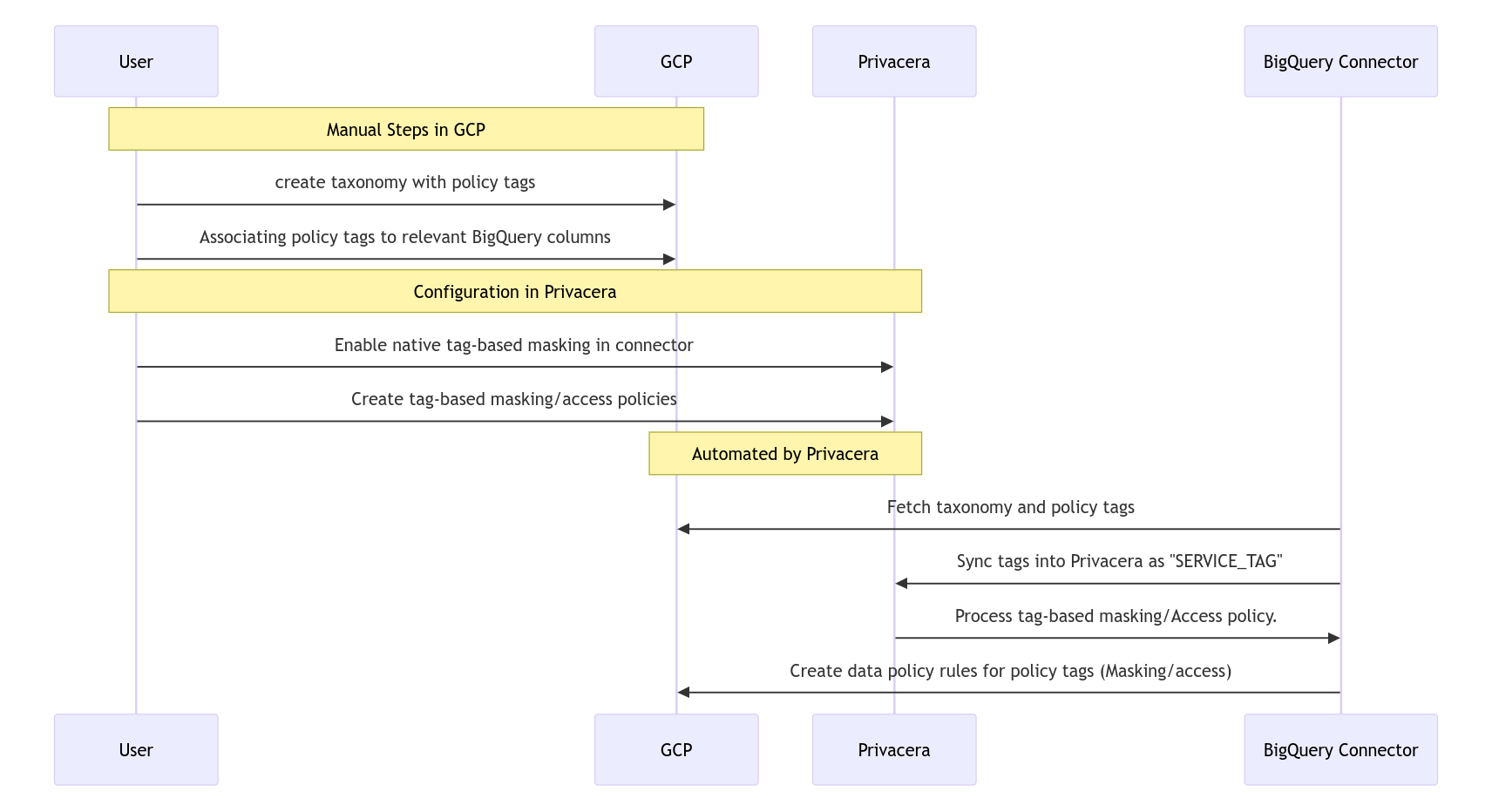
Walkthrough Videos¶
Video 1: Manual Steps to Perform in GCP and Privacera¶
This video outlines the Manual actions required in both GCP and Privacera, including:
- Creating a taxonomy and policy tags
- Associating policy tags to relevant BigQuery columns
- Configuring the Privacera BigQuery connector with native tag-based masking enabled

Video 2: Steps Handled by Privacera¶
This video highlights the automation performed by Privacera, such as:
- Tag Synchronization from BigQuery to Privacera.
- Processes tag-based masking/access policies and automatically pushes them to GCP as Data policy rules

Tag Synchronization from BigQuery to Privacera¶
The BigQuery Connector automatically synchronizes policy tags from BigQuery into the Privacera Portal. These tags are imported as Service Tags, which are read-only within Privacera. Service Tags are used in evaluating access control and data masking policies.
Service Tags¶
Service Tags are read-only metadata tags that originate from external data service platforms and are automatically synchronized with Privacera. These tags cannot be created, modified, or deleted through the Privacera Portal, as they are managed exclusively at the service level.
Service Tags can be used in tag-based access control and data masking policies, allowing administrators to enforce service-specific access rules, implement consistent data protection strategies, and align access controls with the native tagging mechanisms of each integrated service.
How It Works¶
- The connector pulls tags from BigQuery and creates them in Privacera using the following format:
Hierarchical Tag Example¶
- If BigQuery tags are structured hierarchically, the connector flattens the hierarchy while preserving the full path of each tag. This approach ensures tag uniqueness and maintains consistent policy evaluation within Privacera.
For example, a taxonomy may be structured as:
The connector will create three separate tags in Privacera as follows:
org/{org-id}/projects/{project-id}/locations/us/taxonomies/{taxonomy-id}/policyTags/parent-tag
org/{org-id}/projects/{project-id}/locations/us/taxonomies/{taxonomy-id}/policyTags/parent-tag/child-tag
org/{org-id}/projects/{project-id}/locations/us/taxonomies/{taxonomy-id}/policyTags/parent-tag/child-tag/grand-child-tag
This flattened structure preserves the original tag hierarchy while ensuring compatibility with Privacera’s Service Tag model.
📖 Reference: Working with Tag Hierarchies in BigQuery
Viewing Synced Service Tags from BigQuery¶
You can view all service tags synchronized from BigQuery to Privacera by following these steps:
- Navigate to Access Management → Tag Management
- Select the SERVICE TAG tab to view all tags retrieved from BigQuery and synchronized by the connector.
This section allows users to verify that tags from BigQuery, including hierarchical tags, are properly imported and available for policy creation in Privacera.
Prerequisites¶
-
Taxonomy and Policy Tag Creation
- The BigQuery connector pulls tags directly from Google BigQuery, where all tags are organized within a taxonomy. Therefore, creating a taxonomy along with corresponding policy tags is a mandatory prerequisite for using this feature.
- Follow the links below for detailed steps to create them manually in BigQuery:
Create Policy Tag and Taxonomy in BigQuery
-
Policy Tag-to-Column Association in BigQuery
- The BigQuery connector enforces tag-based access and masking policies using policy tags defined in BigQuery, together with the policies configured in Privacera.
- To ensure these policies take effect for end-users, the corresponding policy tag must be associated with the relevant column in BigQuery.
Note: Before creating tag-based access or masking policies in Privacera, ensure the policy tag is properly associated with the target column in BigQuery.
-
Organization ID Configuration
The Organization ID is a mandatory configuration parameter required for tag-based masking functionality. This identifier specifies the GCP organization where policy tags are created and managed.
Required Configuration
Ensure the Organization ID is correctly configured in the connector settings to prevent issues with tag synchronization and policy enforcement.
To retrieve your Organization ID refer Google Cloud Documentation - Retrieving Organization ID.
- In the Self-Managed Portal, navigate to Settings → Applications → BigQuery Connector.
- Configure the following property under ADVANCED tab:
- On the Privacera Manager host, navigate to the connector configuration YAML:
- Add or update the following property:
-
Connector Configuration
To enable this feature, ensure the connector is properly configured using the advanced configuration . Follow the configuration guide here: Native Row Filter and Tag Masking Setup -
Custom Masking: To create a masking policy using a custom routine (UDF), the routine must already exist in the project where the masking policy is to be applied. Additionally, users are required to provide the routine path.
The Path of routine must follow following format:
| Text Only | |
|---|---|
Key Considerations:
- The routine must be present within the same project where the masking policy is being created.
- The path format should be strictly followed to ensure proper integration of the routine with the masking policy.
- Ensure that
<project-id>is accurate. - Ensure that
<dataset-name>is valid in the project. - Ensure that
<routine-Name>matches exactly with the routine created in the dataset.
- Ensure that
- If the provided routine path is not supported or the routine is not found, the connector will throw an error and create the masking policy in BigQuery with the default masking.
Use Cases¶
Applying Tag-Based Masking Policy for End User¶
This guide outlines the steps to create a tag-based masking policy in Privacera for end users, including applying access and masking policies.
Assumption
Before proceeding, ensure you have completed the steps listed in the Prerequisites section and that the following setup exists in BigQuery:
- A policy tag
test_tagis created under the taxonomytest_Taxonomywith taxonomy ID12345678.- The tag exists in project
test_project-12345under organization ID123123.- The policy tag
test_tagis associated with theSSNcolumn of thetest_tablein BigQuery.- Security Zone Consideration: If you plan to control permissions using Security Zones, note that the Security Zone should be configured only at the project level (i.e., test_project-12345) to ensure consistent enforcement across all tagged resources within the project.
Step 1: Create Resource-Based Policies in Privacera¶
- Create Resource-Based Policy for Job Creation Access:
- Policy Type: Resource-Based Policy
- Resource: Test_Project
- Permission: Job Create
- Users: test_user1,test_user2
- Create Resource-Based Policy for Query Permission on Table:
- Policy Type: Resource-Based Policy:
- Resource: Test_Table
- Permission: Query
- Users: test_user1,test_user2
Step 2: Create Tag-Based Masking Policy in Privacera¶
- Navigate to the tag Masking policy creation page
- Locate and enable the Service Based Tags toggle switch
- Once enabled, three dropdown menus will appear in sequence:
- Service Type: Select the type of service as Google BigQuery)
- Service: Choose the specific service instance by default its 'privacera_bigquery'
- Tag Type: Select the type of tag as Policy Tag.
- Add service tag ,users and masking option
- Tag:
org/123123/projects/test_project-12345/locations/us/taxonomies/12345678/policyTags/test_tag - Users: test_user1
- Component: bigquery
- Masking Option: Nullify
- Tag:
- For more details please refer Tag policy Creation
This policy masks the SSN column in the test_table for test_user1 by replacing its values with NULL. This ensures sensitive data remains protected for the specified user.
Step 3: Create Tag-Based Access Policy in Privacera¶
- Navigate to the tag Access policy creation page
- Locate and enable the Service Based Tags toggle switch
- Once enabled, three dropdown menus will appear in sequence:
- Service Type: Select the type of service as Google BigQuery)
- Service: Choose the specific service instance by default its 'privacera_bigquery'
- Tag Type: Select the type of tag as Policy Tag.
- Add service tag ,users and masking option
- Tag:
org/123123/projects/test_project-12345/locations/us/taxonomies/12345678/policyTags/test_tag - Users: test_user2
- Component: bigquery
- Permission:
Query
- Tag:
- For more details please refer Tag policy Creation
This policy will grant test_user2 access to query the data tagged with forward_camera_186122_priv_tag_id. Since test_user2 has the appropriate access policy, they will be able to see the unmasked data, regardless of any masking policies applied for other users.
Note: The access granted to test_user2 will bypass any masking policies for that specific tag, allowing full visibility of the data.
 Limitations¶
Limitations¶
-
BigQuery Column-Level Security Behavior: In BigQuery, if an end user needs access to a column that has a tag attached, they must either be included in the tag-based masking policy or have permissions through a tag-based access policy. This is a key requirement for managing column-level security with tags in BigQuery.
Reference: BigQuery Column-Level Security -
Location Supported in Connector’s Configuration:
- BigQuery resources and taxonomies can be created across various locations. However, the PolicySync connector currently supports access control management for resources within a single location.
- The connector does not support the management of resources across multiple locations concurrently.
- Prev Connector Guide